Microsoft Purview eDiscovery provides your organisation with the ability to discover data for internal, legal, and regulatory investigations. Its increased abilities over the years have led Microsoft to align its eDiscovery tool to the Electronic Discovery Reference Model (EDRM), delivering a complete end-end solution designed for discovering, holding, processing, and exporting. For clarity the eDiscovery solutions available differ by licence; eDiscovery Standard (E3) and eDiscovery Premium (E5). In this blog, I will be using eDiscovery Premium for my examples. In addition to an eDiscovery license, users who are scoped within a Compliance Boundary must be configured with an Exchange Online license.
Countless multi-national organizations and Governments are required to incorporate eDiscovery to ensure Electronically Stored Information (ESI) is available as evidence in lawsuits and investigations. In addition, should already have in place technical boundaries to control who can search for what data in which regions, government agencies and in other cases business departments. This is often due to internal compliance needs, regulatory requirements or data sovereignty laws that state each region, agency or business department must be implemented within technical walls to prevent cross-region, cross-agency and/or cross-departmental discovery of data. To accomplish this in M365, Microsoft offers Compliance Boundaries.
Compliance Boundaries is a solution based on RBAC Groups and Security Permissions Filtering. The RBAC Groups manage the m365 eDiscovery permissions of who can access a Compliance Boundary. The Security Permissions Filtering controls the content locations that can be searched within the configured Compliance Boundary. Combined this enables the business to create the technical boundaries within which eDiscovery & Admins:
- Search for content
- Preview search results
- Export search results
- Purge items (soft delete by default)
In this blog, I will describe my experiences and the scenarios where Compliance Boundaries have been deployed together with Multi-Geo, Tiered eDiscovery Teams & Business Departments.
Before I go into detail about implementing Compliance Boundaries, there are a couple of points we need to take into consideration.
- the version of eDiscovery adopted; Standard or Premium
- whether your organisation has Multi-Geo enabled
For eDiscovery Standard
Without Multi-Geo enabled, all searches executed in Standard are tenant wide.
With Multi-Geo enabled and eDiscovery Standard, all searches and exports are performed in the geo-location of where the search is executed. However, this may not meet the requirements of your organisation, therefore, if you require eDiscovery admins to be able to search outside of their region and to be able to export into this region, this can be achieved by using the -Region parameter.
For eDiscovery Premium
Without Multi-Geo enabled, all searches executed in Premium are tenant wide.
With Multi-Geo enabled and eDiscovery Premium, it will search the whole tenant regardless of where the search is executed. As a result, this can cause compliance issues and as a result, where I have seen Compliance Boundaries deployed the most.
Moreover, with Multi-Geo and creating the security filters, you can map the mailbox attributes you require (see below notes for more details on supportability). More importantly, you will need to take into consideration the SharePoint & OneDrive for Business Satellite locations specified in the URL as this plays a part in building the Permissions Filters designed for segmenting the searches intended for regional Compliance Boundaries. These will look something like this: –
- SharePoint Online: HTTPS://<Tenant><GeoLocationCode>.sharepoint.com
- OneDrive for Business: HTTPS://<Tenant><GeoLocationCode>-my.sharepoint.com
There are four main steps to configure Compliance Boundaries: –
- Identity a User Attribute to differentiate source anchors
- Requires an attribute(s) or a source anchor to be associated with Mailboxes, SharePoint & OneDrive Sites
- Create a Role Group for each region or department
- Requires a Roles Based Access Group to home the regional eDiscovery Managers
- Create Search Permissions to enforce the boundaries
- Required to map the permissions filters to the attribute and RBAC Role
- Create a Case for the Compliance Boundary Created
- Required to ensure the configuration is successful
Compliance Boundaries & Multi-Geo
Now, let us explore how to create a Compliance Boundary with eDiscovery Premium based on Multi-Geo for geographical locations.
- Note: At the time of writing, Security Filters can only be configured using PowerShell commands.
- Note: Downloads for all PowerShell Commands are at the bottom of this post.
For the regions APAC & EMEA, we are going to create two Compliance Boundary Roles and the equivalent Security Filters. I am going to include the locations of, Japan, & Singapore for APAC and Great Britain & Switzerland for EMEA. These are only a selection of the available geo-tags available from Microsoft. A complete list of Geo’s is referenced below in the Multi-Geo link.
APAC eDiscovery Group
The RBAC Role Group configuration. Initially, you can either copy the eDiscovery Manager Role from the Permissions Blade in the Compliance Centre with all its permissions, rename and save it. Or you can use the following PowerShell Commands to achieve the same: –
- $roles = (Get-RoleGroup “eDiscovery Manager”).roles | ForEach-Object {$_.split(“/”)[$_.split(“/”).count-1]}
- New-RoleGroup –Name “Compliance Boundaries for APAC” -Description “Compliance Boundaries for APAC Regions eDiscovery Managers” -Roles $roles
APAC Permissions Filter
The Security Filtering configuration. Our regional example command will look like the following: –
- New-ComplianceSecurityFilter -FilterName “Compliance Boundaries for APAC Regions eDiscovery Managers” –Description “Compliance Boundaries for APAC Regions eDiscovery Managers” –Users “Compliance Boundaries for APAC” –Filters “Mailbox_C -like ‘TOK*’ -or Mailbox_C -like ‘SIN*'”,”Site_Path -like ‘companydomainJPN.sharepoint.com -or Site_Path -like companydomainAPC.sharepoint.com’ -or Site_Path -like ‘companydomainJPN-my.sharepoint.com -or Site_Path -like companydomainAPC-my.sharepoint.com'” –Action All
EMEA eDiscovery Group
The RBAC Role configuration. As above, you can either copy the eDiscovery Manager Role from the Permissions Blade in the Compliance Centre with all its permissions, or you can use the following PowerShell Commands: –
- $roles = (Get-RoleGroup “eDiscovery Manager”).roles | ForEach-Object {$_.split(“/”)[$_.split(“/”).count-1]}
- New-RoleGroup –Name “Compliance Boundaries for EMEA” -Description “Compliance Boundaries for EMEA Regions eDiscovery Managers” -Roles $roles
EMEA Permissions Filter
The Security Filtering configuration. Our regional example command will look like the following: –
- New-ComplianceSecurityFilter -FilterName “Compliance Boundaries for EMEA Regions eDiscovery Managers” -Description “Compliance Boundaries for EMEA Regions eDiscovery Managers” -Users “Compliance Boundaries for EMEA” -Filters “Mailbox_C -like ‘GBR*’ -or Mailbox_C -like ‘CHE*'”,”Site_Path -like ‘companydomainGBR.sharepoint.com’ -or Site_Path -like ‘companydomainCHE.sharepoint.com’ -or Site_Path -like ‘companydomainGBR-my.sharepoint.com’ -or Site_Path -like ‘companydomainCHE.sharepoint.com'” -Action All
Command Breakdown
Let me breakdown what the command is doing: –
New-ComplianceSecurityFilter is the command associated with the solution
-Description, which I am sure speaks for itself, after that, we have the
-Users, this is not the end users you want to add to the filtering, it is the eDiscovery Admins that need to be positioned here which must include the RBAC group created above (or you have created), then we have the
-Filters, these are the actual Mailbox, SharePoint and OneDrive for Business Filters you require to be available for searching, Mailbox_C is the Mailboxes CountryOrRegion Property name and the Site_Path is the URL of the SharePoint or OneDrive URL. Lastly, we have the
-Action, this is the permissions Compliance Security Filter Action Type required as detailed below on what actions the eDiscovery Manager can perform. The current list of actions is as follows: –
- Export: The filter is applied when exporting search results or preparing them for analysis in eDiscovery Premium.
- Preview: The filter is applied when previewing search results.
- Purge: The filter is applied when purging search results. The PurgeType parameter value on the New-ComplianceSearchAction cmdlet controls how the items are deleted. The default value is SoftDelete, which means the purged items are recoverable by users until the deleted items retention period expires.
- Search: The filter is applied when running a search.
- All: The filter is applied to all search actions.
Compliance Boundaries for Tiered eDiscovery Groups & Regional Departments
Additionally, my experiences have shown there are a few other ways businesses may look to organise their search and two of the most common are outlined below, namely the use of Tiered eDiscovery Groups and a breakdown by Business Departments, which I have also shared below.
Tiered eDiscovery Groups
In some cases, it has also been necessary to deploy the solution to meet internal processes requiring a tier-based approach to running the discovery workflow from beginning to end.
For example:
- 1st Line eDiscovery Admins can: only execute a search
- 2nd Line eDiscovery Admins can: review and interact with those search results
- 3rd Line eDiscovery Admins can: export those results
This can happen within the same region or can be part of a global workflow. Let us explore how to create a Compliance Boundary based on regional business structures and/or processes.
The RBAC Role configuration. Once again, first up, you can either copy the eDiscovery Manager Role from the Permissions Blade in the Compliance Centre with all its permissions, or you can use the following PowerShell Commands: –
1st Line eDiscovery Group
- $roles = (Get-RoleGroup “eDiscovery Manager”).roles | ForEach-Object {$_.split(“/”)[$_.split(“/”).count-1]}
- New-RoleGroup –Name “Compliance Boundaries First Line eDiscovery Group” -Description “Compliance Boundaries for Legal Department First Line eDiscovery Admins” -Roles $roles
2nd Line eDiscovery Group
- $roles = (Get-RoleGroup “eDiscovery Manager”).roles | ForEach-Object {$_.split(“/”)[$_.split(“/”).count-1]}
- New-RoleGroup –Name “Compliance Boundaries Second Line eDiscovery Group” -Description “Compliance Boundaries for Legal Department Second Line eDiscovery Admins” -Roles $roles
3rd Line eDiscovery Group
- $roles = (Get-RoleGroup “eDiscovery Manager”).roles | ForEach-Object {$_.split(“/”)[$_.split(“/”).count-1]}
- New-RoleGroup –Name “Compliance Boundaries Third Line eDiscovery Group” -Description “Compliance Boundaries for Legal Department Third Line eDiscovery Admins” -Roles $roles
The Security Filtering configuration. Our tiered example command will look like the following: –
1st Line eDiscovery Group Filter
- New-ComplianceSecurityFilter -FilterName “First Line eDiscovery APAC Compliance Boundaries Filter” -Description “Compliance Boundaries First Line APAC eDiscovery Admins” -Users “Compliance Boundaries First Line eDiscovery Group” -Filters “Mailbox_C -like ‘APC*'”,”Site_Path -like ‘companydomainAPC.sharepoint.com’ -or Site_Path -like ‘companydomainAPC-my.sharepoint.com'” -Action Search
2nd Line eDiscovery Group Filter
- New-ComplianceSecurityFilter -FilterName “Second Line eDiscovery APAC Compliance Boundaries Filter” -Description “Compliance Boundaries Second Line APAC eDiscovery Admins” -Users “Compliance Boundaries Second Line eDiscovery Group” -Filters “Mailbox_C -like ‘APC*'”,”Site_Path -like ‘companydomainAPC.sharepoint.com’ -or Site_Path -like ‘companydomainAPC-my.sharepoint.com'” -Action Preview
3rd Line eDiscovery Group Filter
- New-ComplianceSecurityFilter -FilterName “Third Line eDiscovery APAC Compliance Boundaries Filter” -Description “Compliance Boundaries Third Line APAC eDiscovery Admins” -Users “Compliance Boundaries Third Line eDiscovery Group” -Filters “Mailbox_C -like ‘APC*'”,”Site_Path -like ‘companydomainAPC.sharepoint.com’ -or Site_Path -like ‘companydomainAPC-my.sharepoint.com'” -Action Export
Regional Business Departments
Additionally, I have found use cases to also expand Compliance Boundaries aimed at business departments. In each main region a business operates from, a dedicated SharePoint Site has been created for this department due to the sensitive nature of the content stored here. Consequently, these sites must remain strictly searchable for eDiscovery Managers situated within that department & region. A good example of this is a Legal Department, many laws can be adopted globally. However, there are instances where local data sovereignty laws apply, in which case Compliance Boundaries are effective.
Let us explore how to create Compliance Boundaries for APAC & EMA Legal Departments.
APAC Legal Department Group
The RBAC Role configuration. Yet again, you can either copy the eDiscovery Manager Role from the Permissions Blade in the Compliance Centre with all its permissions, or you can use the following PowerShell Commands: –
- $roles = (Get-RoleGroup “eDiscovery Manager”).roles | ForEach-Object {$_.split(“/”)[$_.split(“/”).count-1]}
- New-RoleGroup –Name “Compliance Boundaries for APAC Legal Department” -Description “Compliance Boundaries for APAC LEGAL Department eDiscovery Managers” -Roles $roles
APAC LEGAL Department Filter
The Security Filtering configuration. Our departmental example command will look like the following: –
- New-ComplianceSecurityFilter -FilterName “Compliance Boundaries Filter APAC LEGAL Department Only” -Description “Compliance Boundaries APAC LEGAL Department Only” -Users “Compliance Boundaries for APAC Legal Department” -Filters “Site_Path -like ‘companydomainAPC.sharepoint.com/sites/LEGAL’” -Action All
EMEA LEGAL Department Group
The RBAC Role configuration. Yet again, you can either copy the eDiscovery Manager Role from the Permissions Blade in the Compliance Centre with all its permissions, or you can use the following PowerShell Commands: –
- $roles = (Get-RoleGroup “eDiscovery Manager”).roles | ForEach-Object {$_.split(“/”)[$_.split(“/”).count-1]}
- New-RoleGroup –Name “Compliance Boundaries for EMEA LEGAL Department” -Description “Compliance Boundaries for EMEA LEGAL Department eDiscovery Managers” -Roles $roles
EMEA LEGAL Department Filter
The Security Filtering configuration. Our departmental example command will look like the following: –
- New-ComplianceSecurityFilter -FilterName “Compliance Boundaries Filter EMEA LEGAL Department Only” -Description “Compliance Boundaries EMEA LEGAL Department Only” -Users “Compliance Boundaries for EMEA LEGAL Department” -Filters “Site_Path -like ‘companydomainEU.sharepoint.com/sites/LEGAL’” -Action All
Compliance Boundaries Shared Experiences
Throughout the deployment I have worked on I have seen several challenges with the solution, and I will share them with you now.
Shared MS-Teams Across Regions
If your organisation uses Microsoft Teams and have Teams shared across regions, this presents a challenge for discovering data. For example, if I am in Europe (Geo-Code: EUR) and a Teams Channel has been shared with me that was created in North America (Geo-Code: NAM), I am joining a Team that is outside of my technical boundary. Consequently, this creates an issue when searching for data I will have a Compliance Boundary that the EMEA eDiscovery Managers only can search. This means that when you execute a search it will only bring back the data for the users and sites you have access to. As a result, you have no way of searching the other region unless your discovery process includes a request for a look-up of data within the opposing region, or the eDiscovery Manager must be included in the opposing region where the Teams data is located for the time the case is open and then removed afterwards.
Just in Time Access
There have been times when a requirement for the RBAC Group(s) to be granted on a when-needed basis. Although PIM does not yet support the Purview Compliance Centre Roles, you can use the workaround in Nikki Chapple’s blog here: – https://nikkichapple.com/how-to-apply-just-in-time-access-to-security-compliance-roles/ [1]
Leavers & Licenses
If a user leaves the organisation and the eDiscovery License is removed from this user, they fall out of the scope of Compliance Boundaries and will, therefore, be available for searching without restrictions.
Exclusions in Filtering
Microsoft does not recommend using filters for exclusions for example -not. I have worked with a colleague to undo the -not exclusions as this caused several issues when executing searches.
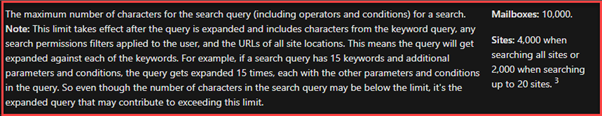
Search Limitations with Permissions Filtering
Be careful of the number of search filters you create as they count towards the search query character’s limits: –
[1] Nikki has an excellent blog on Compliance & Governance, If you would like more information, Nikki can be found on Twitter: @ChappleNikki
Helpful Links
Set up compliance boundaries for eDiscovery investigations
Configure permissions filtering for eDiscovery
Filterable properties for the RecipientFilter parameter on Exchange cmdlets
New-ComplianceSecurityFilter
Microsoft 365 Multi-Geo availability
To Conclude
I hope this information has been helpful and clarified how Compliance Boundaries are designed and configured. As always, I am happy to hear any feedback.
PowerShell Commands
All categories have been organised for ease of reading when opening with Notepad ++